Yet another plugin for mangoblog! About two weeks ago, I rediscovered Project Honeypot.They have a service called HTTP:BL, where you can check ip addresses for comment spamming and email harvesting behaviour.
With the help of that service, you can now block those ip addresses from even seeing your blog. This will reduce comment spamming, reduce server resources, and helps protecting the content of your site, especially any email addresses you might have on your blog.
What it does is simple: before the template of your website is executed, the ip address of the visitor is checked. If it is a spammer or harvester, your custom message will be displayed, and the request will be aborted.
Download the plugin
You can download it with the following url: http://www.railodeveloper.com/svn.cfm?repositorypath=honeypotSpamBlocker/HoneypotSpamBlocker.zip%3AHEAD&download=1
You can also view and download the source code in my subversion browser
Settings
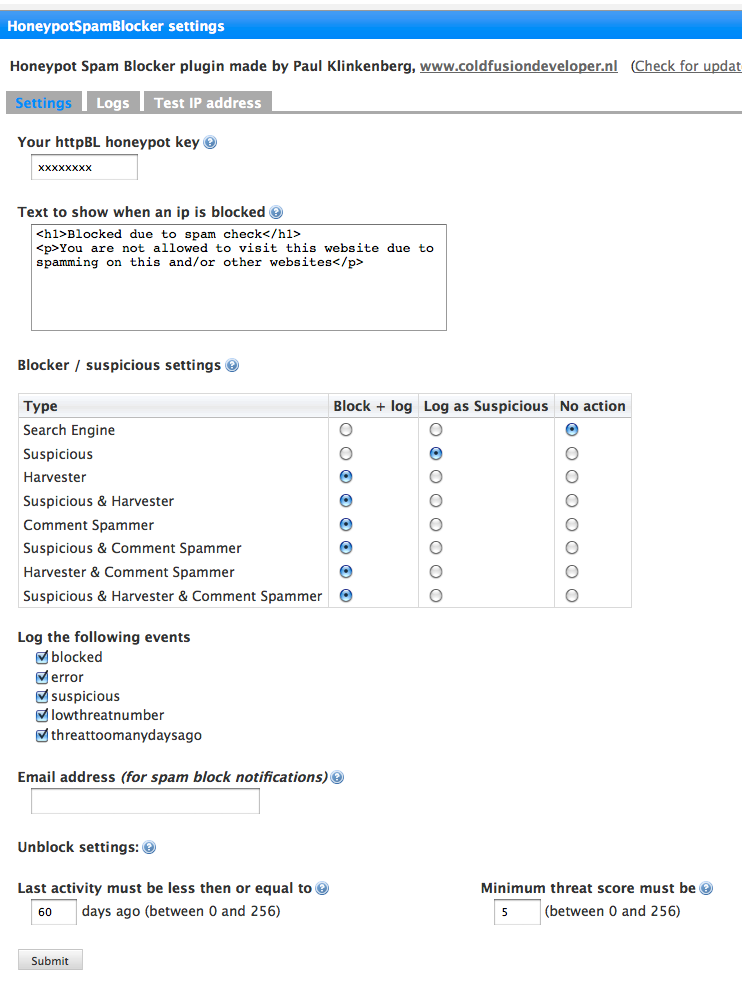 As you can see in the screenshot, there are a lot of settings. You can define which types of spammers are blocked, which are just logged, and even filter on last spam activity and threat rating by HTTP:BL.
As you can see in the screenshot, there are a lot of settings. You can define which types of spammers are blocked, which are just logged, and even filter on last spam activity and threat rating by HTTP:BL.
Just click on the image to see a larger version.
Log files
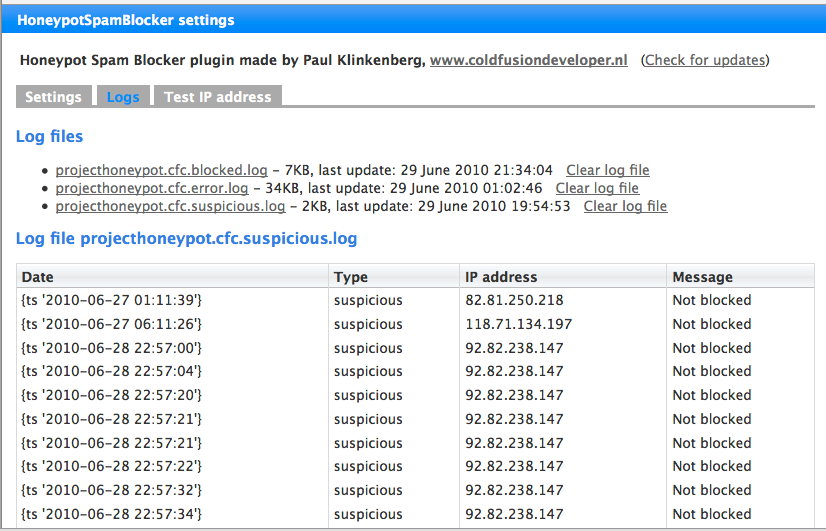 In the settings you can define which types of events are logged. If you are logging anything, you can view the log from within the plugin settings page.
In the settings you can define which types of events are logged. If you are logging anything, you can view the log from within the plugin settings page.
Test it
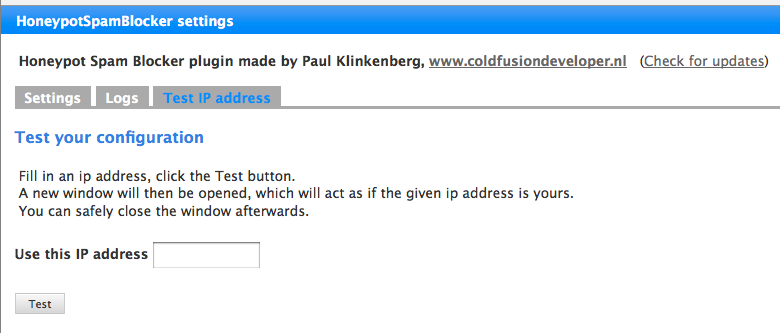 Because your ip is probably not spamming or harvesting, you need a way to test this plugin. Therefore, there is also a test screen within the settings page. Just enter an ip address and hit the button. A new window will then open which will act as if you are visiting your blog with that ip. You can find some spam ip addresses from the project honeypot website.
Because your ip is probably not spamming or harvesting, you need a way to test this plugin. Therefore, there is also a test screen within the settings page. Just enter an ip address and hit the button. A new window will then open which will act as if you are visiting your blog with that ip. You can find some spam ip addresses from the project honeypot website.
Problems? Want to say thanks?
Leave me a comment; I appreciate it!
| Viewed 9203 times






#1 by Sami Hoda - June 30, 2010 at 12:45 AM
#2 by Mark Aplet - June 30, 2010 at 12:53 AM
I do like all the settings you have given users to control the action to be taken on a comment. I am hoping it works well with the existing plugin to double to protection.
Also, on a related note. I created a plugin for putting a honeypot on your blog in an effort to catch spammers too. Take a look at it here: http://www.visual28.com/articles/project-honey-pot
#3 by Paul Klinkenberg - June 30, 2010 at 10:10 AM
Simply said: if a spammer never sees your comment form, then it will also not submit anything against it. So this plugin is more radically in the frontline.
@Mark: I rewrote and enhanced a cfc found on http://www.mximize.com/fighting-comment-spam-with-project-honeypot, and am planning to create a blog post about the cfc itself as well in the near future. This plugin can be used together with cfformprotect, no problem. See reply to Sami. I would encourage everyone to use the cfformprotect plugin btw, because it has soo much more checks to filter out spam.
Thanks for the compliment, and I indeed saw and download your plugin. Only thing for me was, that it uses the exact 9 example html pieces which are given by Project Honeypot, and I am convinced that a good harvester bot writer would be able to filter those 9 strings out of any html. Therefor, I wrote a new "Project Honeypot Link Generator": http://www.coldfusiondeveloper.nl/post.cfm/link-generator-coldfusion-project-honeypot, which makes the links more random. Maybe, if you have time, you could incorporate that into your plugin? Then I would sure use it :-)
Thanks for the comments!
#4 by Mark Aplet - June 30, 2010 at 4:16 PM
#5 by Sami Hoda - June 30, 2010 at 6:00 PM
Good stuff. Can't wait to try it out!
#6 by Paul Klinkenberg - July 1, 2010 at 11:52 PM
#7 by Mark Aplet - July 8, 2010 at 11:39 PM
#8 by Paul Klinkenberg - July 9, 2010 at 1:39 PM
But good to know; I will change it shortly!
#9 by Laura - July 9, 2010 at 9:56 PM
#10 by Paul Klinkenberg - July 9, 2010 at 11:30 PM
Curious to find out what the problem is, but no clue how to find it out, since I haven't faced the problem :-/
#11 by Mark Aplet - July 10, 2010 at 1:01 AM
Am I right about this Laura?
#12 by Laura - July 10, 2010 at 3:51 AM
The installer changes the name of the folder with the name of the plugin, so it doesn't matter what the expanded folder looks in the beginning.
Paul,
One way to check would be to make a cfhttp request and see what the content and headers are.
#13 by Sami Hoda - July 22, 2010 at 9:46 PM
#14 by Paul Klinkenberg - July 22, 2010 at 11:21 PM
Now, I just switched my hostname from coldfusiondeveloper.nl to railodeveloper.com, so if you copied the download path in this post, and if Mangoblog does not allow redirects while downloading a plugin, then that was the problem.
I'd say: try again, with this link: http://www.railodeveloper.com/svn.cfm?repositorypath=honeypotSpamBlocker/HoneypotSpamBlocker.zip:96&download=1
If it doesn't work, let me know! I did check it, and I just get a "200 OK" with the zip data.
#15 by WebmasterAlex - August 11, 2010 at 7:00 PM
Great Plugin! Congrads!
All though PHP(Project Honeypot) is a very good source for checking the IPs against it, I have been doing some research on this for over a year of logs on my install of Mango. PHP Database is not updated as often as other community Databases, like StopForumSpam for example, but that is besides the point.
One thing that cuts down a lot of Running to the other network to check is to check if CGI.SERVER_PROTOCOL of the incoming request is HTTP/1.0, and if so throw a CAPTCHA at the visitor before checking the IP against PHP or other source.
Most of Comment spammers are using Proxies to do the dirty job and are not really Humans, but Bots. They do pass CFID and CFTOCKEN though.
And If the question is Answered properly, Set a UNIQUE Cookie for the USER and let the User in. This logic could go into OnRequestStart method in Application.cfc.
I find it that cuts down on about 95% of the need to call BAD IP Validation scripts.
There are legitimate USE of HTTP/1.0 and is utilized by some SPIDERS like Slurp and Corporate Proxy servers that run via SQUID, but if the Captcha presented properly, Users understand. Some of the Mobile Devices run via HTTP/1.0 as well.
But the Cookie does the Job pretty well.
Just A thought.
Alex
#16 by Paul Klinkenberg - August 11, 2010 at 9:11 PM
#17 by Paul Klinkenberg - August 11, 2010 at 9:13 PM
This particular project is stopping spammers at the front door, not when submitting a comment. So giving http-1.0-visitors a captcha image instead of the actual website would be a bit much ;-)
Thanks again for the tips, Paul
#18 by kristof polleunis - February 6, 2011 at 1:13 AM
http://devnulled.com/software/cfakismet/
http://wordpress-plugins.feifei.us/hashcash/
#19 by Paul Klinkenberg - February 6, 2011 at 1:50 PM
Cheers, Paul